[Writeup] BITSCTF Remember me (forensics 60)
This challenge provides a compressed file with a .sav extension. Running file gives nothing useful (data). Running strings gives more interesting output:
$ strings remember_me.sav | less
VirtualBox SavedState V2.0
Unit
Build Type
release
Host OS
win.amd64
...
So we have a VirtualBox saved state file. Some searching around suggested that Volatility doesn’t support this format.
After some more searching around, this writeup popped up. Surprisingly the Dropbox link was still functional, and even more surprisingly the code compiled and (after changing some hard coded filenames) worked! It dumped some files and then crashed, but most importantly we had both the display screenshot and the main memory.
Running the screenshot parser (which also worked!) produced the following picture:
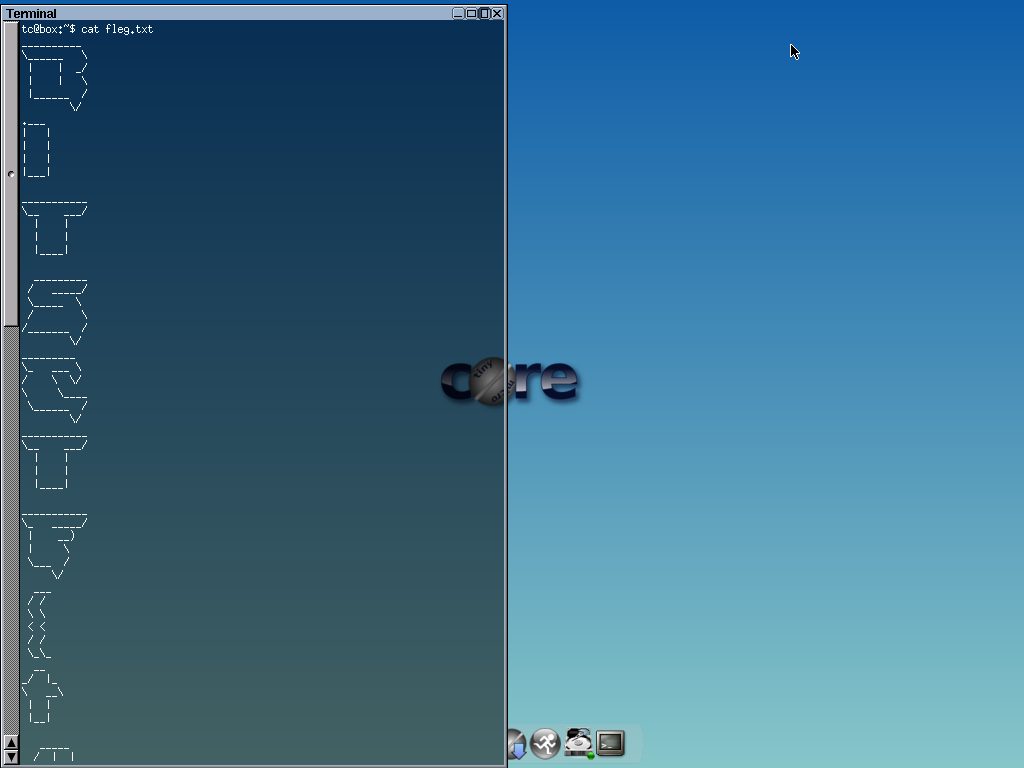
So we know the flag is in memory, which we have in remember_me.sav-pgm.out. Time to dig out my trusty hex editor and search for underscores.
The first few hits are not useful, but finally at 0xEA7319 we get something very interesting:

Extracting the hex values from 0xEA7319 to 0xEA793D into a new file and cat’ing gives (draws) the flag.
BITSCTF{t4k1ng_a_dump}