Jun 17, 2019
This weekend is Google CTF, running all day Saturday and Sunday! If you’ve not had a chance to participate in a real CTF with us yet, this will be a great opportunity, with challenges ranging from beginner to super-difficult-with-massive-prizes. For those of you that came to our event last week, it’ll be a great opportunity to put your skills into practice and compete against thousands of teams online – and help Oxford keep its place on the UK leaderboards.
We’ve booked the Oxford Foundry again on Saturday from 11am-3pm to meet up in person and do some challenges together. We’d love to see you there – if you can’t make it, join us on our Slack channel! If you want to come in person, please let us know at this link so we have an idea of numbers.
Mar 15, 2019
We (Mary, Richard, Alastair, Louise, David and Sai) headed to the University of Southampton last Saturday 9th March to participate in the Higher Education Cyber Challenge (HECC). With no InterACE running this year, Southampton took up the mantle and did a brilliant job of running a jeopardy-style CTF for UK Academic Centres of Excellence in Cyber Security.
We put two teams in and enjoyed a day spent tackling a range of fun and interesting challenges, ranging from the hardcore reverse engineering types to manipulating audio files to going out to the car park to search for RFID tags. Between us we had widely varying experience and skillsets, and were pleased to find there were plenty of different types and levels of challenge that we were all able to have a go at!
The whole day had a great atmosphere, with 26 teams competing from universities across the UK, and we look forward to the next iteration.
Oct 25, 2018
This year BSides is in Delhi, but though we couldn’t fly out there, the online CTF was accessible around the world. After a good result last year we were keen to have another go this time around — and introduce some of our new members to a real competition.
 Crafting a file-read exploit in the background, XOR cribbing in the foreground
Crafting a file-read exploit in the background, XOR cribbing in the foreground
With a good turnout we made progress on several of the challenges during the group session, with the number slowly climbing through the evening.
Jan 27, 2018
The University of Cambridge once again ran its Inter-ACE workshop on binary exploitation, repeating the successful event hosted in 2017. We joined students from all over the country to hone our (very rusty) pwning skills with the help of veteran hacker Graham Rymer.
 Late morning - ASLR is back on
Late morning - ASLR is back on
Over the course of the day Richard, Mary, Romy, Andrew, Mark and Klaudia got their hands dirty with some stack overflow vulnerabilities. With modern mitigations (canaries, ASLR, non-exec stack) turned off this isn’t too hard, but quickly the challenge ramped up. By the end Graham was demonstrating a return-orientated programming exploit that updated the GOT entry for the puts library function to execute shellcode with the mitigations back on.
 Drinks afterwards and not a recruiter in sight
Drinks afterwards and not a recruiter in sight
Apr 5, 2017
On 18 March, three teams from Oxford headed to Cambridge to participate in the second annual Inter-ACE competition. The three teams were Ox002147 (Alastair, Cecile, Emma, Ilias), 0xO02147 (Chris, Dennis, Richard, Will), and 0x0O2147 (Freddie, Louise, Mariam, Mary).
 The competition room - Oxford teams next to the exit door
The competition room - Oxford teams next to the exit door
Upon arriving, the information session made clear that we were about to embark on a red-teaming security exercise, with a forensics
side-challenge. Here was the first problem: none of us had the first clue about red-teaming. So, during the competition, once we actually
managed to get nmap running over OpenVPN (after accidentally scanning half the eduroam network a few times… hint: don’t use Windows) we were staring at already captured hosts. With no obvious thing to do, we buckled down on the forensics. We actually did pretty well on it, and team Ox002147 was 3rd for a decent amount of time!
 They moved that giant flag whenever we lost 3rd place - it was kinda annoying
They moved that giant flag whenever we lost 3rd place - it was kinda annoying
Once there was just one hour left, they turned the scoreboards off (and took the giant flags away) so we had no idea how we were doing, or how we had finished after it was all over. After the competition there was a formal dinner at Trinity College, which was easily the best part of the day (4 different types of wine!).
Then came the awards ceremony - sadly we didn’t get 3rd place, but we did for some reason (allegedly for “innovation, thinking outside the box, and making the best use of their abilities”) get the je ne sais quoi award!
 On sait pas pourquoi
On sait pas pourquoi
The prize itself was a pretty cool device with colourful LEDs which light up differently depending on how you press the buttons.
In all, it wasn’t too bad, but it would have been nice to know about the competition format beforehand. At least now we know what to expect next year, and hopefully we’ll be able to put up more of a fight.
But much sooner than that, we have…
Cambridge 2 Cambridge Qualifier
Cambridge2Cambridge is another annual competition, an apparently “more richly endowed” event of which Inter-ACE is part of, so to speak. This time students from both UK ACE-CSRs and selected US universities can compete. The event itself takes place in Cambridge on 24-26 July, but to attend one must first qualify. The top 3 teams at Inter-ACE qualify automatically, and since we weren’t part of that exclusive group we had to participate in the C2C qualifier on 1 April and place well amongst the UK participants to guarantee attendance.
The qualifier was a classic jeopardy style CTF, but an individual one - every person for themselves. And we smashed it, with Ilias and Emma taking the top 2 UK spots (3rd and 4th overall) and an estimated 10 Oxonians with a solid chance of directly qualifying for the final. A pretty good Oxford showing!
Feb 15, 2017
Over the past weeks we’ve participated in several online CTFs, and it seemed a bit overkill to write a dedicated post for each one. Instead, here’s an overall summary.
Final position: 13th (out of 275)
Final position: 4th (out of 110)
Final position: 10th (out of 531)
Feb 12, 2017
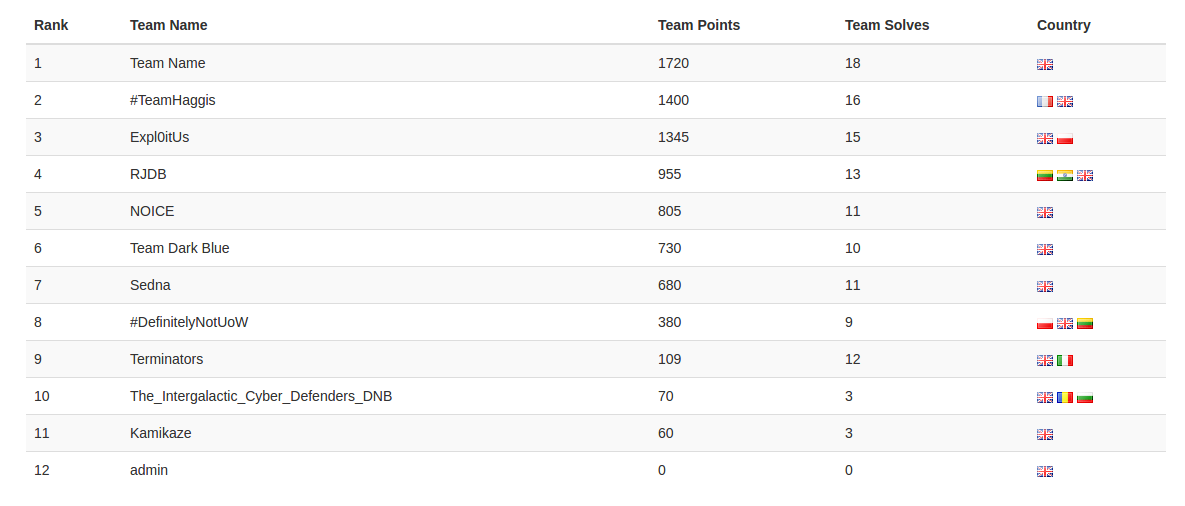
On the 11th of Feb, Oxford entered two teams into the University of Westminster Novice CTF, organised by Cyber Security Challenge UK. The CTF was sponsored by Raytheon and BT and targeted at novices / first time competitors. The competition jeopardy style, with a focus on forensics, crypto and generic puzzles.
Team “Dark Blue”, composed of Mary, Mariam, Louise and Ari came in a respectable 6th place. Team “Team Name”, composed of Olivia, Thomas, Will and Dennis came in 1st place. Both Oxford teams were taking part in their first official CTF, having previously been given some tips and tricks by Ilias, and enjoyed the day immensely.
“Team Name” each won a set of lockpicks and a copy of the Red Team Field Manual. Somewhat bizarrely, they were also awarded a team prize: 1 copy of
“Java: The Complete Reference Ninth Edition”, a weighty 1300 pages, which was donated to the CDT library.
The final rankings were as follows:
Feb 5, 2017
This challenge provides a compressed file with a .sav extension.
Running file gives nothing useful (data). Running strings gives more interesting output:
$ strings remember_me.sav | less
VirtualBox SavedState V2.0
Unit
Build Type
release
Host OS
win.amd64
...
So we have a VirtualBox saved state file. Some searching around suggested that Volatility doesn’t support this format.
After some more searching around, this writeup popped up.
Surprisingly the Dropbox link was still functional, and even more surprisingly the code compiled and
(after changing some hard coded filenames) worked!
It dumped some files and then crashed, but most importantly we had both the display screenshot
and the main memory.
Running the screenshot parser (which also worked!) produced the following picture:
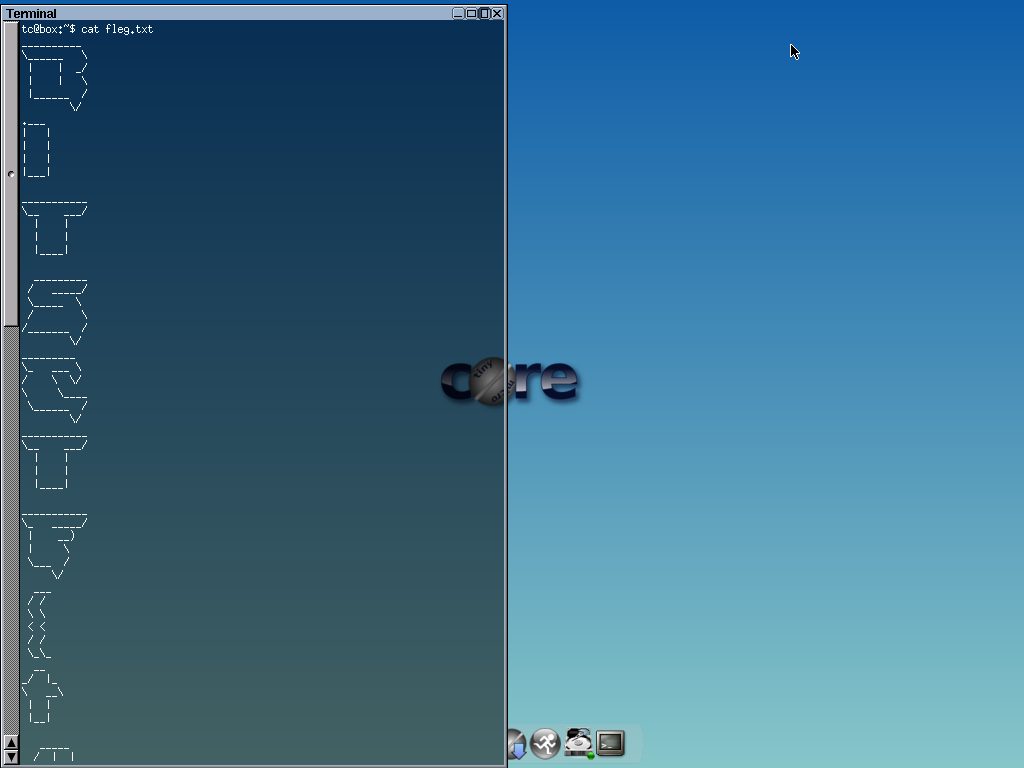
So we know the flag is in memory, which we have in remember_me.sav-pgm.out. Time to dig out my trusty hex editor and search for underscores.
The first few hits are not useful, but finally at 0xEA7319 we get something very interesting:

Extracting the hex values from 0xEA7319 to 0xEA793D into a new file and cat’ing gives (draws) the flag.
BITSCTF{t4k1ng_a_dump}
Dec 20, 2016
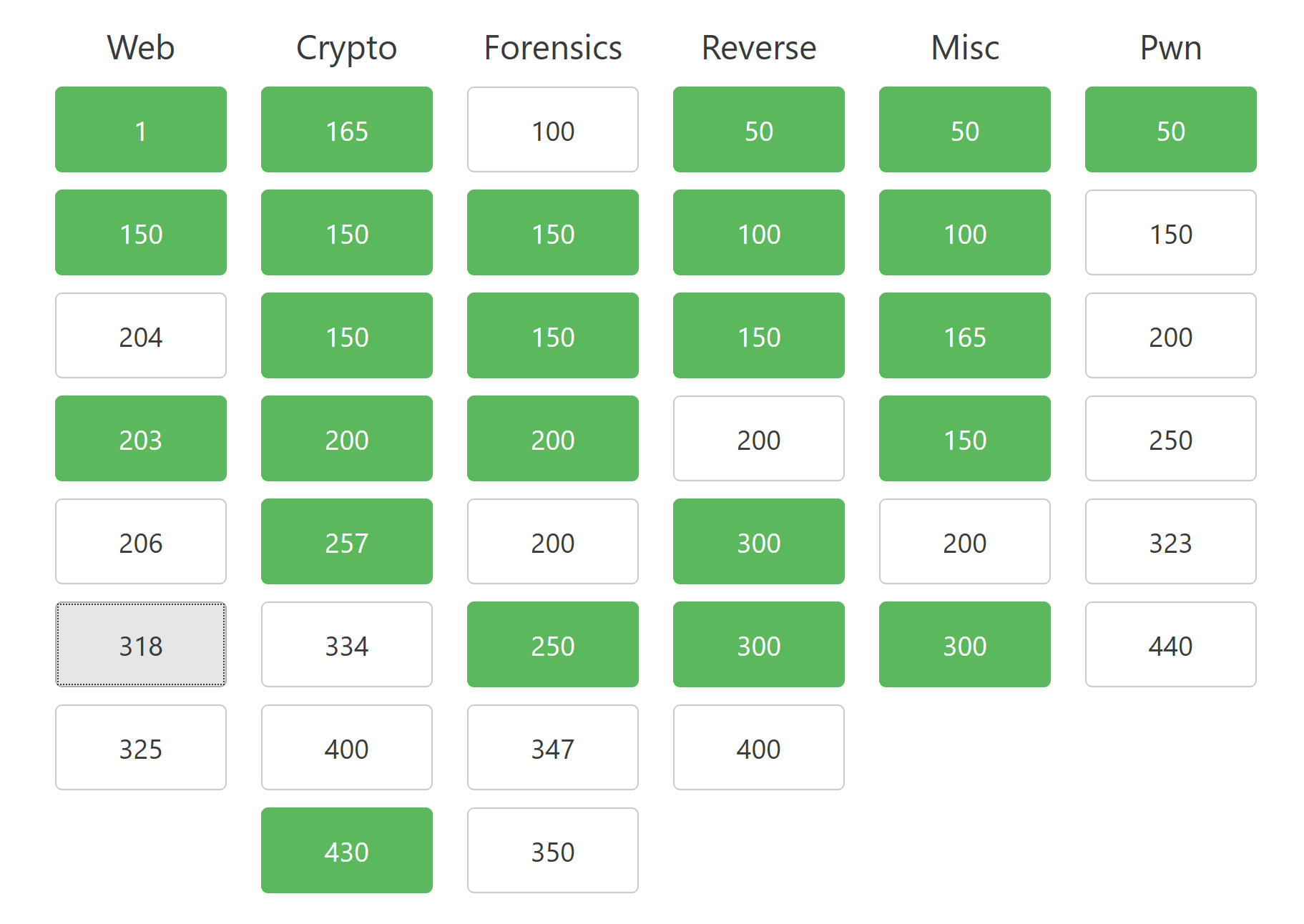
The last competition of the year was Sharif CTF, where
Ilias, Richard, and Alastair placed 13th out of 700 teams after managing to solve 24 out of 42 challenges:
Nov 22, 2016
Having previously qualified in the online round, we (Alastair, Cecile, Chris, Emma, and Ilias) headed to London
to participate in the Deloitte CTF final, with a cool £5000 in prizes to fight for.
The challenges were quite a bit more demanding than the qualifiers, and the competition was fierce, with
Edinburgh getting closer to us and eventually overtaking. The last 4 minutes were intense: we were tied with Edinburgh at 3000
points, but they were leading. Then we submitted one more flag and shot to first place, and watched the clock tick down while
hoping no one else got any more flags… which they didn’t!
Final rankings were as follows:
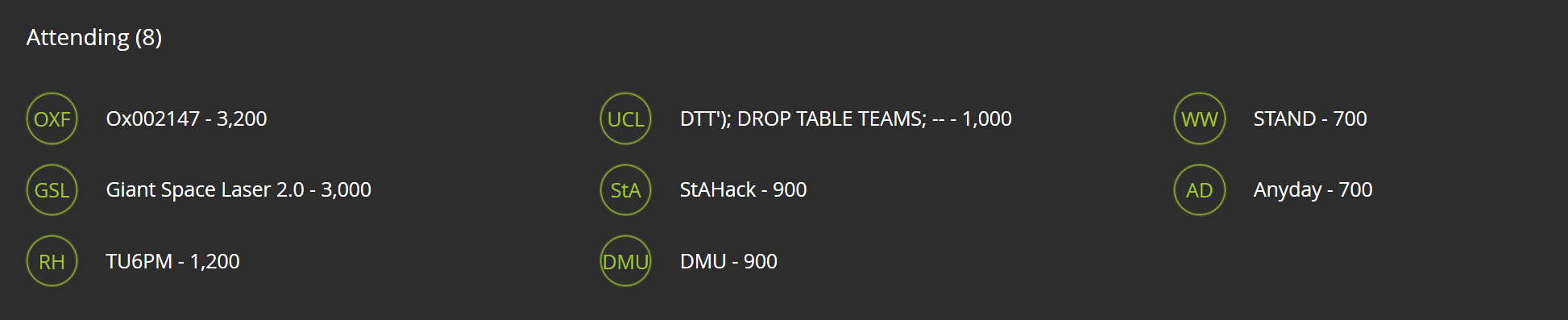
We solved 10 out of 17 challenges:
And here is the team, with an awesome check!

Nov 12, 2016
A team of six members (Alastair, Cecile, Chris, Emma, Ilias, and Richard) participated in the Varsity CTF organized by
BAE Systems and hosted simultaneously at both Oxford and Cambridge by their respective Engineering Societies.
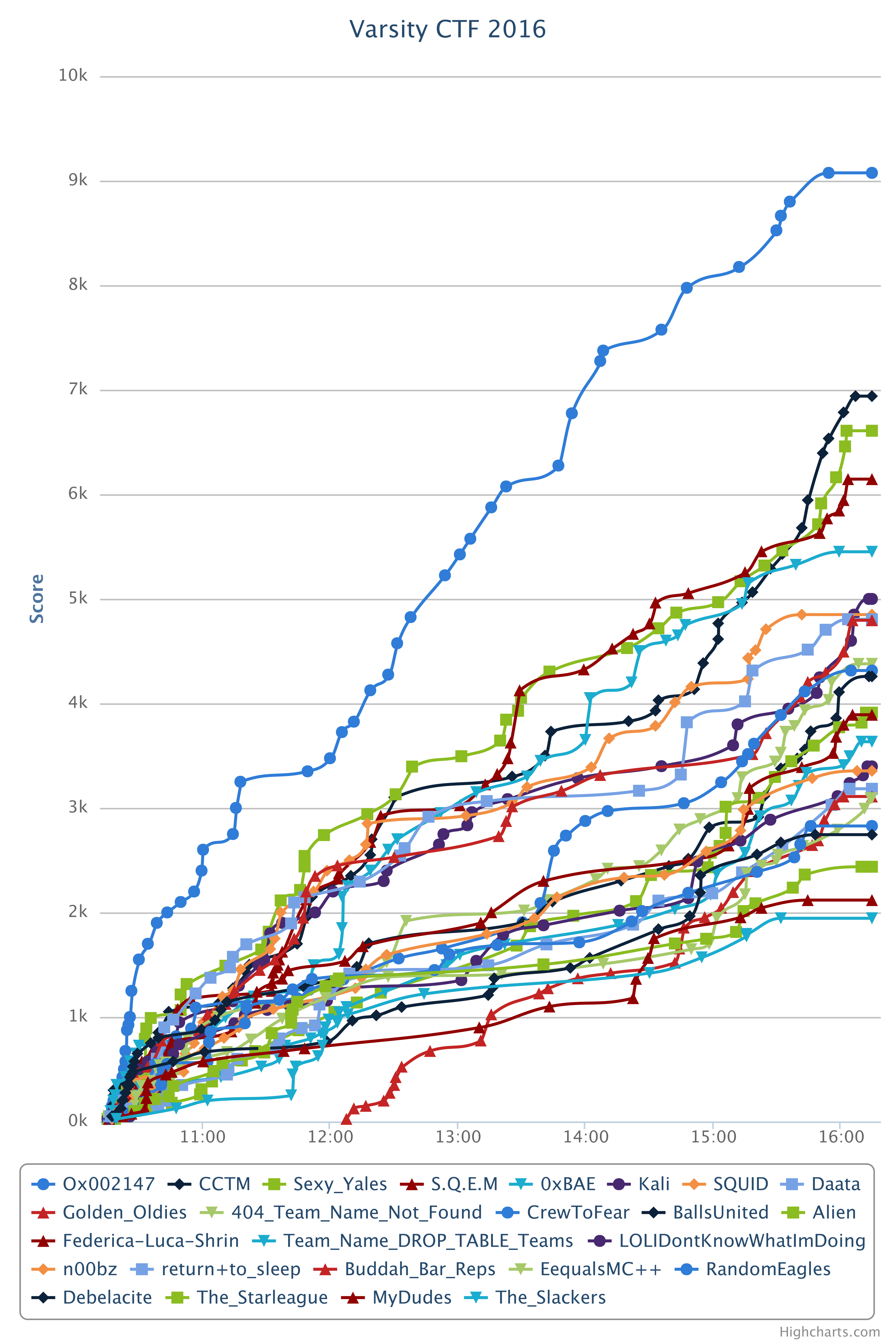
We took the lead early and kept widening the gap with the other teams, as shown by the score graph below.
Team photo, including prizes and Sophos stash!

 Crafting a file-read exploit in the background, XOR cribbing in the foreground
Crafting a file-read exploit in the background, XOR cribbing in the foreground Late morning - ASLR is back on
Late morning - ASLR is back on Drinks afterwards and not a recruiter in sight
Drinks afterwards and not a recruiter in sight The competition room - Oxford teams next to the exit door
The competition room - Oxford teams next to the exit door They moved that giant flag whenever we lost 3rd place - it was kinda annoying
They moved that giant flag whenever we lost 3rd place - it was kinda annoying On sait pas pourquoi
On sait pas pourquoi







